Two Factor Authentication (2FA)
What is Two-Factor Authentication?
Two-factor authentication adds a second layer of security to your online accounts. Verifying your identity using a second factor (like your phone or other mobile device) prevents anyone but you from logging in, even if they know your password.
How It Works
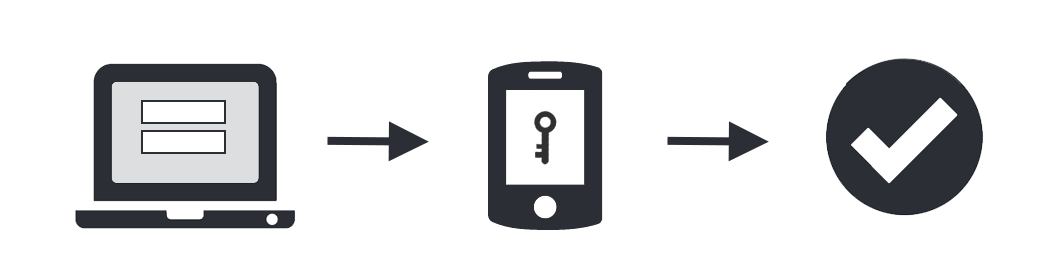
- Enter username and password as usual
- Use your phone to verify your identity
- Securely logged in
Once you’ve enrolled you’re ready to go: You’ll login as usual with your username and password, and then use your device to verify that it’s you. Your administrator can set up the system to do this via SMS, voice call, one-time passcode, the Mobile smartphone app, and so on.
No mobile phone? You can also use a landline or tablet, or ask your administrator for a hardware token. Our software lets you link multiple devices to your account, so you can use your mobile phone and a landline, a landline and a hardware token, two different mobile devices, etc.
Why Do I Need This?
Passwords are increasingly easy to compromise. They can often be stolen, guessed, or hacked — you might not even know someone is accessing your account.
Two-factor authentication adds a second layer of security, keeping your account secure even if your password is compromised. With our software Push, you’ll be alerted right away (on your phone) if someone is trying to log in as you.
This second factor of authentication is separate and independent from your username and password — We never see your password.
Supported Devices
- iOS
- Android
- Windows Phone
- Cell Phones & Landlines
- Hardware Token
How Do I Set It Up?
F.A.Q.
Frequently Asked Questions
It will work on a large number of already established software as well as self hosted systems. i.e. Office 365, Dropbox, VPN connections, Quickbooks on-line, EHR softwares , etc.
2FA is a major step and a requirement for many compliance regulatory systems. The Health Insurance Portability and Accountability Act (HIPAA) recommends using two-factor authentication and strong access controls to help mitigate security risks related to remote access to patient data.
Yes, we can supply full authentication logs including:
Date and time of the access attempt
Authentication Success or Failure, and why
End-user’s username
Which application was accessed
Source IP address and location, if a publicly resolved IP address
Client OS, browser, plugin information, and trusted status
Surprisingly not. Let us give you a demo to show you how easy it works.